{
"token_expiry_seconds": 3600,
"secret": "supersecretvalue",
"host": "0.0.0.0",
"port": 8080,
"worker": 4,
"login_via_otp": false,
"log": {"type": "local"},
"stats: true,
"tls": true,
"max_idle_per_host": 200,
"timezone": "Europe/Paris",
"redis": "redis://redis_server:6379",
"session_cookie": false,
"max_age_session_cookie": 3600,
"ratelimit_auth": {
"burst": 10,
"block_delay": 500,
"requests_per_second": 10
},
"ratelimit_proxy": {
"burst": 10,
"block_delay": 500,
"requests_per_second": 10
},
"users": [
{
"username": "admin",
"password": "$argon2id$v=19$m=19456,t=2...",
"allow": ["192.168.1.0/24", "172.16.54.2"],
"roles": ["Administrator", "read", "write"]
},
{
"username": "alice",
"password": "$argon2id$v=19$m=19456,t=2...",
"roles": ["User", "read", "write"]
}
]
}
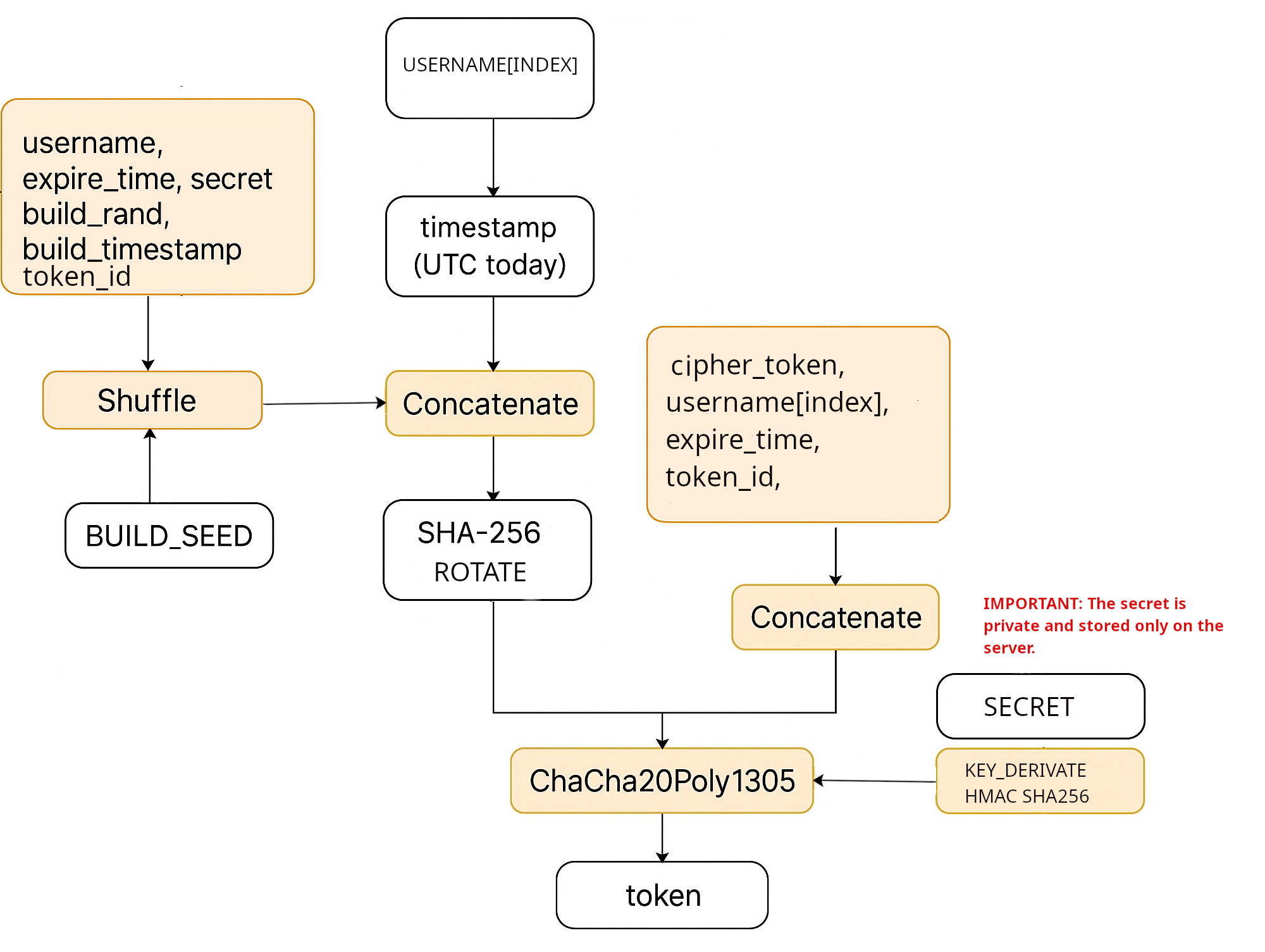
token_expiry_seconds
1-31536000 (Max 5 Years)
Default: 3600
secret
Please generate a secure token (64 characters or more!)
Default: unset
login_via_otp
Enable or disable logging of OTP login attempts.
Valid values: true or false
Default: false
host
IP address where the server listens
Default: 0.0.0.0
timezone
A
timezone defines how a specific region offsets from UTC (Coordinated Universal Time).
you can select a timezone like
Europe/Paris,
UTC, or
America/New_York to properly convert and display timestamps in local time.
[ show all possible value ]
Default: Europe/Paris
port
Valid range: 1–65535
Default: 8080
session_cookie
Enables automatic setting of the session token as a Set-Cookie header after successful authentication.
This allows seamless integration with frontend dashboards without requiring manual token handling.
Type: boolean
Default: false
Note: The cookie is only sent over HTTPS and includes the flags Secure, HttpOnly, and SameSite=Strict.
max_age_session_cookie
Defines the lifetime (in seconds) of the session cookie issued when session_cookie is enabled.
Type: integer
Default: 3600 (1 hour)
Range: 60 – 31536000 (1 minute to 1 year)
• Example: "max_age_session_cookie": 86400
cors_origins
List of allowed origins for Cross-Origin Resource Sharing (CORS).
Requests from these origins will receive appropriate Access-Control-Allow-* headers in responses.
Type: Array of strings – each string must be a valid origin (scheme + host, optionally port).
Default: [] (CORS disabled)
• Example: "cors_origins": ["https://127.0.0.1", "https://demo.proxyauth.app"]
Note: CORS headers are applied dynamically based on the request Origin header.
redis * New
Enables multi-node synchronization of revoked tokens using
Redis.
When enabled:
- Each ProxyAuth node publishes token actions to Redis (e.g.
{token_id}_action)
- Expiration timestamp is stored in
token:{token_id}
- A propagation counter
{token_id}_count is incremented
- Every node periodically pulls Redis updates into LMDB and RAM
This allows full SSO behavior between different services (e.g. APIs and dashboards) with shared token logic.
Redis acts only as a sync bus — LMDB remains the source of truth.
worker
Number of CPUs available
Default: 4
num_instances
Defines the number of ProxyAuth instances to launch.
Combined with the worker setting, this allows horizontal scaling on multi-core systems.
Each instance runs independently and handles its own worker threads.
Default: 2
Note: Total concurrency = num_instances × worker.
• Example: num_instances: 4 with worker: 4 results in 16 concurrent workers.
log
type: local → do not use remote logging
type: loki → use Loki logging {"type": "loki", "host": "127.0.0.1:1234"}
type: http → get logs via HTTP {"type": "http", "max_writes_log": 10000}
Default: local
stats
boolean: true/false → do not use remote stats /adm/stats or proxyauth stats
Default: false
tls
boolean:
true/false → You can enable or disable listening on the HTTPS protocol./div>
Default: false
max_idle_per_host
int: 0-3000 → defines the maximum number of idle (keep-alive) connections that can be kept open per host. This helps optimize performance by reusing connections instead of opening new ones for each request, while also preventing excessive resource usage by limiting the number of unused open connections.
Default: 50
ratelimit_auth
request_per_seconds: 0 for disable the rate limit, Maximum number of authentication requests allowed per second from a single client.
burst: Number of extra requests allowed beyond the per-second rate before blocking is enforced.
block_delay: Time a client must wait (after exceeding limits) before sending new authentication
Default: Disabled
ratelimit_proxy
request_per_seconds: 0 for disable the rate limit, Maximum number of forward proxy requests allowed per second from a single client.
burst: Number of extra requests allowed beyond the per-second rate before blocking is enforced.
block_delay: Time a client must wait (after exceeding limits) before sending forward request inside ProxyAuth
Default: Disabled
users
Array of user objects for authentication.
Key username – Username to use with the /auth route to obtain a token.
Key password – Password to use with the /auth route to obtain a token.
Key allow – (optional) List of allowed IP addresses or CIDR blocks.
If provided, only requests from these IPs will be allowed to authenticate with this user.
• Example: "allow": ["192.168.1.0/24", "10.0.0.1"]
Key roles – (optional) Array of roles assigned to the user.
These roles are injected into the HTTP header x-user-roles on each proxied request, allowing backends to implement role-based access control.
• Example: "roles": ["Administrator", "write", "read"]